How To Hybrid! - AWS Systems Manager Patch Management
This content is more than 4 years old and the cloud moves fast so some information may be slightly out of date.
As AWS Cloud adoption becomes more widespread throughout the industries, challenges arise how to govern IT resource usage and implement a coherent management for systems across on-premises and the AWS Cloud. This blog post gives insights in how the AWS offered Systems Manager capabilities could be extended from the cloud environment to your hybrid and on-premises environments.
On-premises environment for hybrid governance
Let’s look at the environment we want to centrally govern, by adding AWS Systems Manager functionality. I have prepared two Linux servers within the on-premises environment to simulate a compliant and a non-compliant resource for this blog post. Shown in the below diagram are these two servers:
- Ubuntu 20.04.3 LTS – Installation with most recent patches installed
- Ubuntu 18.04.2 LTS – Installation with patch status as installed on release day in 2019
Within this blog post I will describe the main steps to centrally govern on-premises resources from within AWS Systems Manager and put a highlight on the AWS Systems Manager Patch Manager feature for automatically scanning for available Linux system patches and populating a corresponding patch status compliance dashboard.
Steps to hybrid patch management
To work with AWS Systems Manager, it is necessary to prepare your environment with the AWS Systems Manager Agent which comes preinstalled on all current AWS EC2 Images but needs to be manually installed on your on-premises assets. Following the agent installation is the configuration within the AWS Management Console to reach our goal for this blog post of hybrid patch management.
Install AWS SSM Agent onto on-premises instance
Installation of the AWS Systems Manager is straight forward and will here be highlighted for the installation on an ARM64 based Ubuntu server, a comprehensive installation guide for other Linux distributions, CPU architectures or Windows operating systems can be found in the AWS Documentation.
-
Download AWS Systems Manager Agent Installation package to your Linux Server
wget https://s3.eu-central-1.amazonaws.com/amazon-ssm-eu-central-1/latest/debian_arm64/amazon-ssm-agent.debThis S3 location points to the eu-central-1 (Frankfurt) AWS region and might be adapted to a local region closer to your on-premises network to reduce network latency.
-
Install the AWS Systems Manager Agent package onto your Linux Server
sudo dpkg -i amazon-ssm-agent.deb -
Create Hybrid Activation within AWS Systems Manager
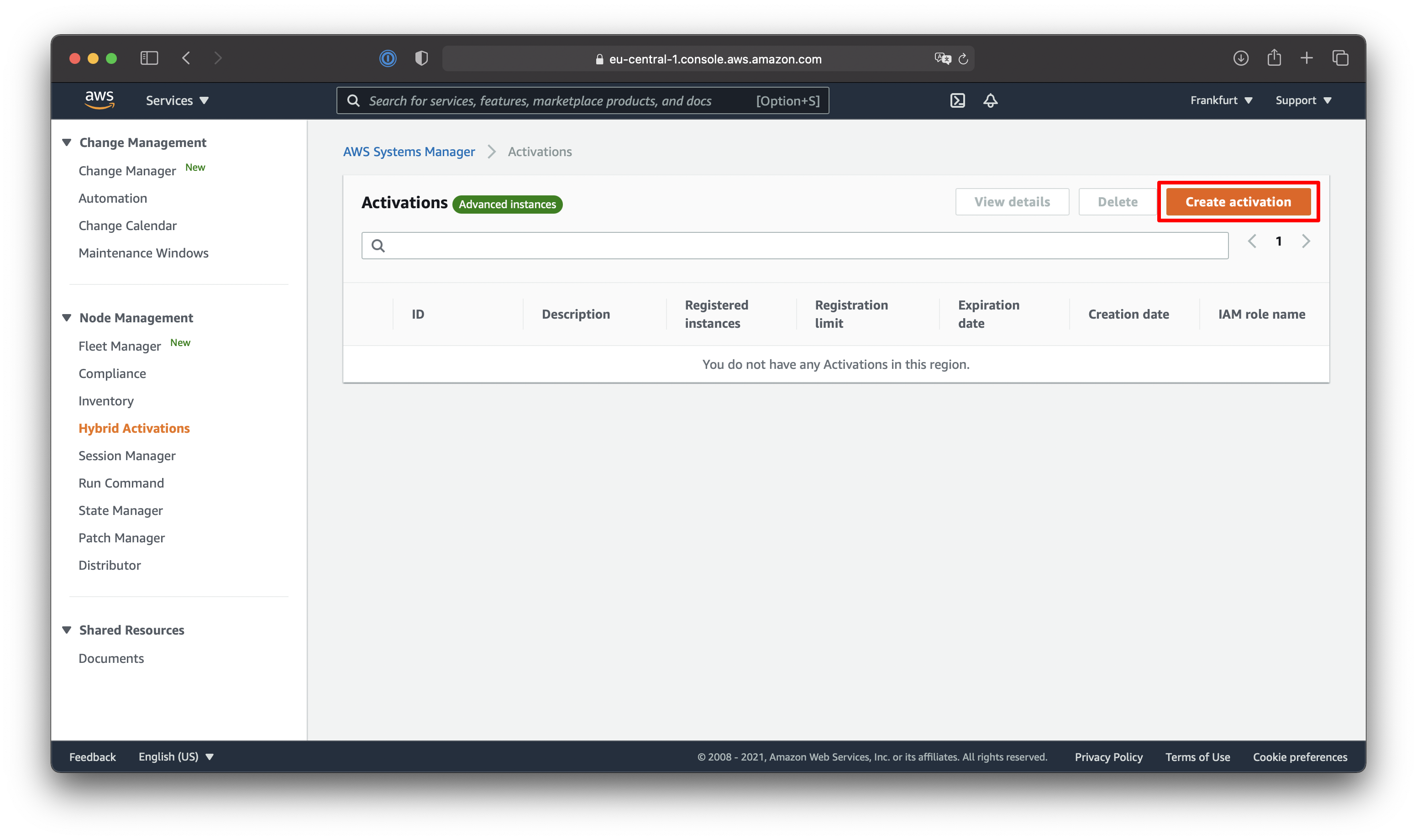
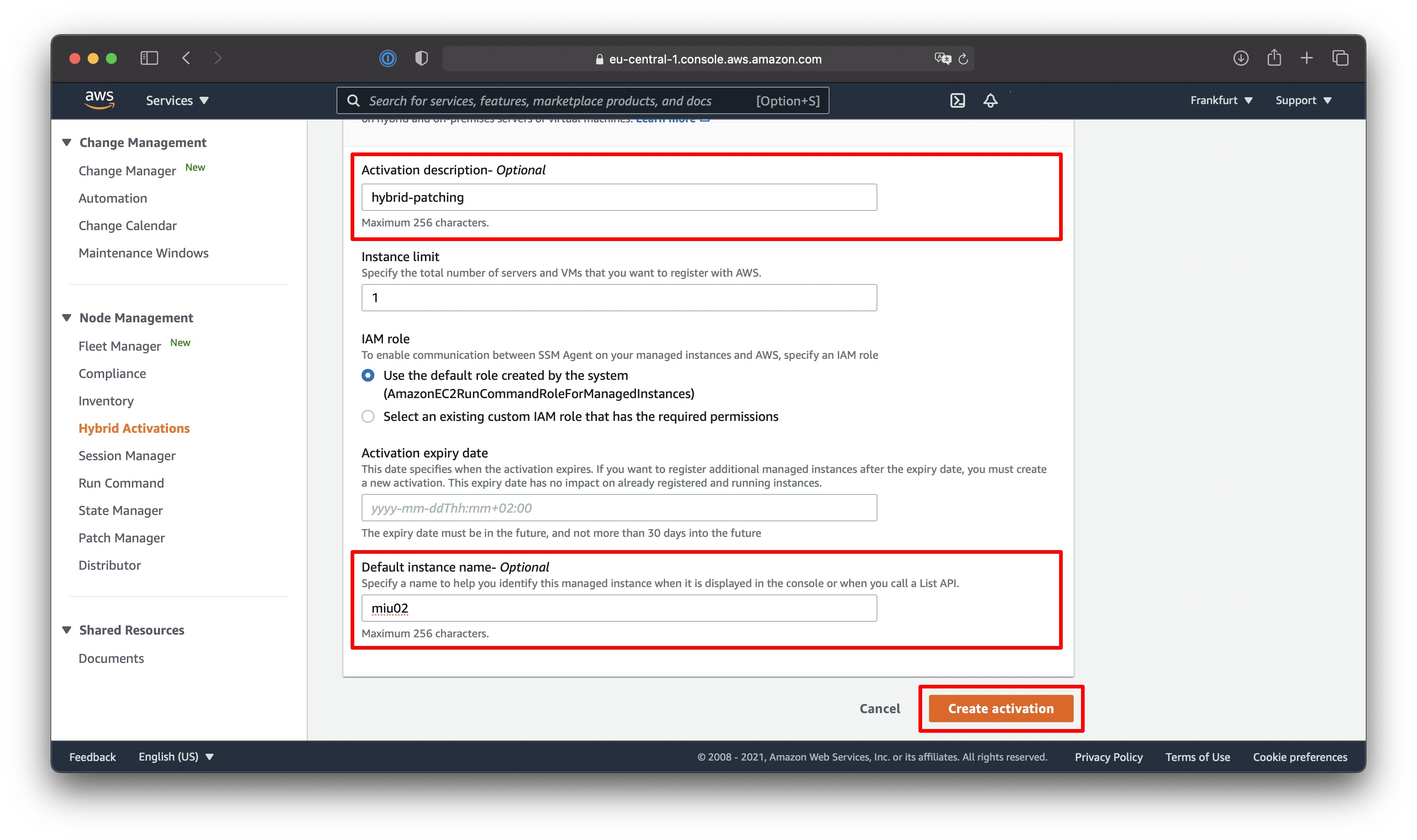
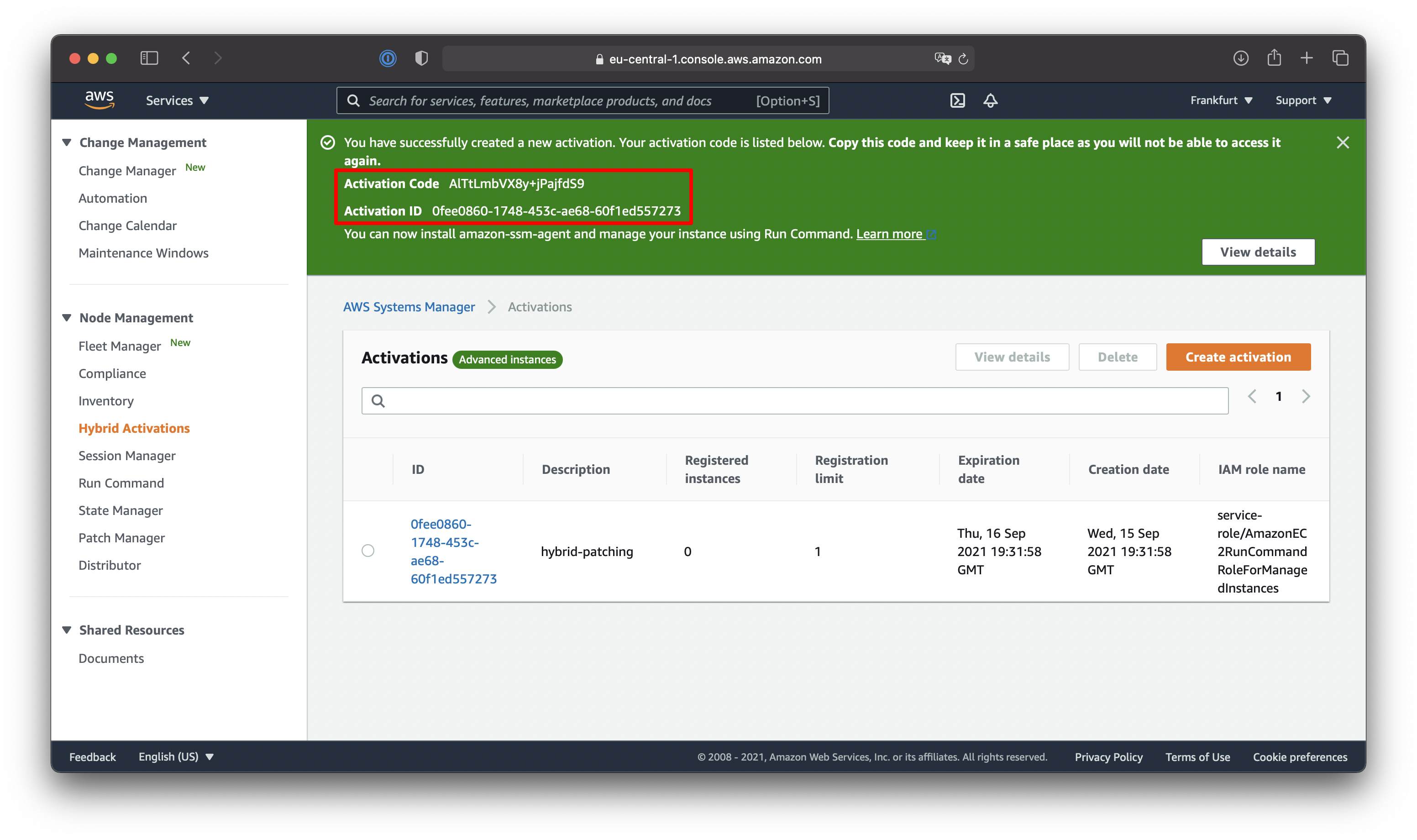
Make sure to note down the Activation Code and Activation ID highlighted within the last screenshot. Be advised not to publicly share that information unless you want people to activate their on-premises instances to your AWS Systems Manager environment.
-
Configure AWS Systems Manager Agent
sudo service amazon-ssm-agent stop sudo amazon-ssm-agent -register -code "activation-code" -id "activation-id" -region eu-central-1 sudo service amazon-ssm-agent start -
Verify AWS Systems Manager Activation within AWS Systems Manager Fleet Manager
To verify that your instance was successfully associated with your AWS Account navigate to the AWS Systems Manager Fleet Manager and view the details page of your newly registered instance.
Use this details page to add tags to your AWS Systems Manager managed instances if you like.
For now, we achieved to install the AWS Systems Manager Agent onto our on-premises instances and configured the agent to connect to our AWS Systems Manager environment as a hybrid activation resulting in a managed instance within our fleet manager. The below diagram shows an overview of that configuration.
Configure AWS Systems Manager Patch Manager Patching
After we made our on-premises instance available within AWS Systems Manager it is important to configure patching within the AWS Systems Manager Patch Manager. Once we reach the AWS Systems Manager Patch Manager overview page within the AWS Management Console, we need to follow the following steps to configure automatic scanning for patches.
-
Hit the Configure Patching button on the overview page of Patch Manager
-
Select that you want to Select instances manually
If you tagged your instances on the Fleet Manager details page of your managed instance you might also decide to select the instances by tag
-
Select to schedule patching within a new maintenance window (Schedule in a new Maintenance Window)
-
Select to Use rate schedule builder and configure to execute the maintenance window every hour
-
Enter an appropriate maintenance window name (e.g., hybrid-patch-scanning)
-
Select Scan only for your patch operations
-
Finalize the patching configuration by hitting the Configure Patching button on the bottom of the configuration page
This will create the maintenance window and will execute the first automatic scan run on your hybrid managed instances. The default patch baseline for the corresponding operating system will be executed and task your hybrid managed instances to report their compliance status to AWS Systems Manager Patch Manager
At this point we have completed the setup of AWS Systems Manager Patch Manager automatic patch status scanning on your hybrid managed instances, giving you a compliance report within the AWS Systems Manager Patch Manager Dashboard for your managed instances, which was the goal of this blog post. Check the diagram below to see all configured AWS features used to achieve hybrid patch governance.
Conclusion
Let’s conclude what we achieved during this blog post as said in the beginning we wanted to achieve automatic scanning for our on-premises Linux servers to report their patch status into a patch compliance dashboard, which we achieved by installing the AWS Systems Manager agent onto our on-premises Linux servers, Creating hybrid activations to make our on-premises servers available as managed instances within AWS Systems Manager and finally configuring patching with the default AWS Systems Manager Patch Manager patchbaselines for the corresponding Linux distributions used within an hourly executed AWS Systems Manager maintenance window. I would call this a success, for our hybrid patch governance from the AWS Cloud!
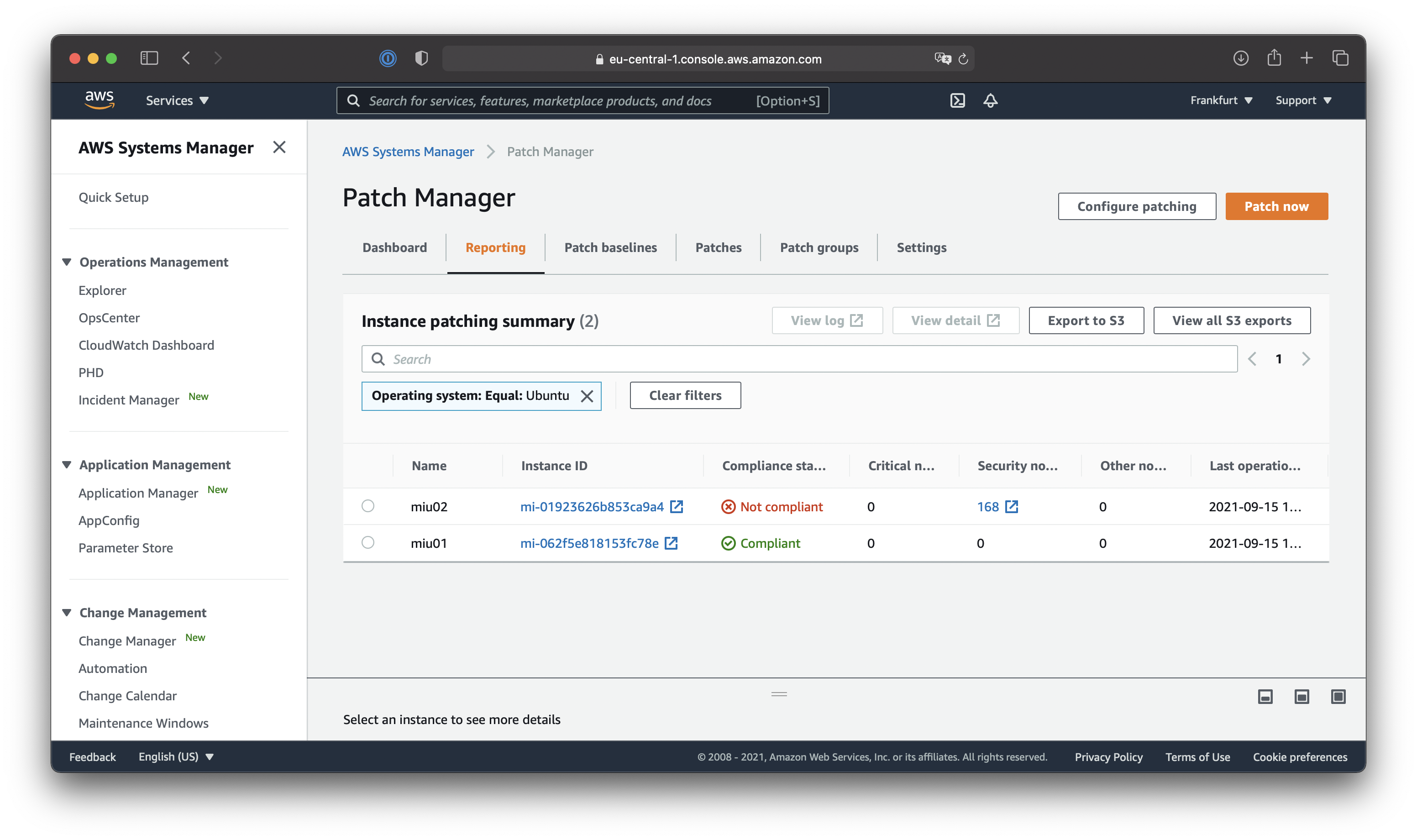
Dashboards and reporting on patch compliance
Additionally, I wanted to show you the patch compliance dashboards within AWS Systems Manager Patch Manager and show you the reporting view. Depending on your hybrid environment the dashboard most probably looks different, but to give you an idea the following screenshots might provide just that.
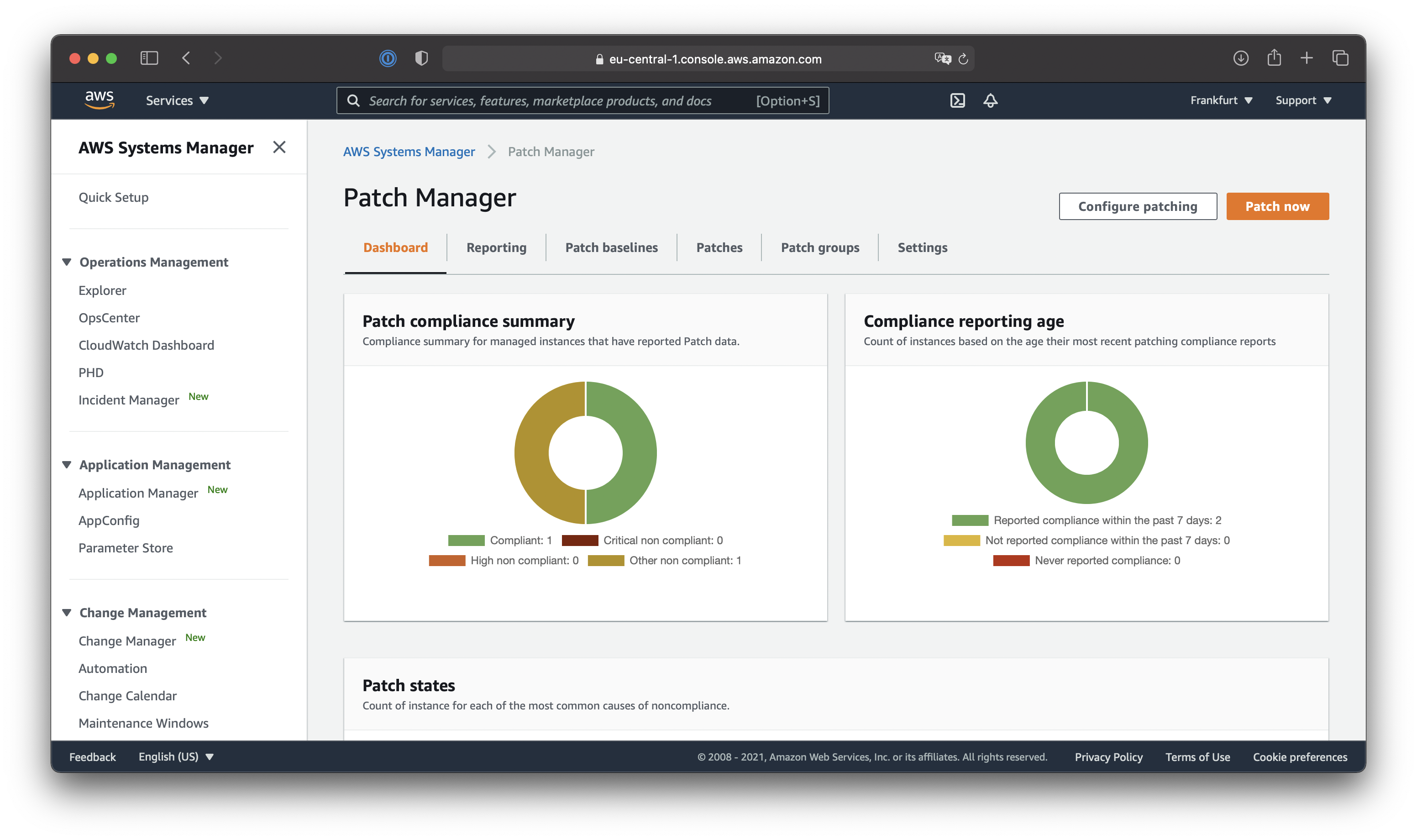
As we just touched the patching functionality within AWS Systems Manager there are more features to explore. So, if you want to learn more about AWS Systems Manager and how to integrate AWS Cloud features into hybrid environments to make IT governance and compliance easier feel free to reach out to me to provide feedback or have a quick chat about your companies needs and if AWS Systems Manager could bring value to your hybrid environment. Who knows there might be some more blogs within the How To Hybrid series coming up!



