Stay single - AWS SSO on the cli with distributed CodeCommit Repositories
TL;DR with aws-sso-util and awsume sso and codecommmit is easy
AWS - CodeCommit Repository for everyone
I am one of the small but growing numbers of persons who use AWS CodeCommit. It’s fast, it’s easy and it’s free for up to 50G and 5 Users.
So with each small private project, I start:
aws codecommit create-repository --repository-name "privateproject" --region eu-central-1
If you work on multiple projects, having the repository in the very account you are working in have the advantage of having code , infrastructure as code and documentation as code(tm) nearby.
Decoupled CodeCommit Repository per Project
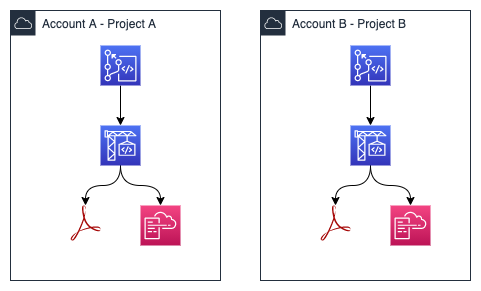
Helper: git-remote-codecommit and awsume
With a MAC OS, you get into trouble using anything which uses keychain and dynamic password. For years this was no fun. Keychain tried to store the temporal credentials as permanent.
But with https://github.com/aws/git-remote-codecommit fun has come back. Install it with
pip install git-remote-codecommit
With git-remote-codecommit installed, you may easily use:
git remote add origin codecommit::eu-central-1://privateproject
But the codecommit uses the current credentials, so if your AWS_SECRET_ACCESS_KEY is of accounta und your repository is in accountb, you have a problem - wrong way!

Right way
The real power of codecommit helper is the possibility to connect the repository with an AWS profile.
So if the local aws profile is “accountb”, you can say:
git remote add origin codecommit::eu-central-1://accountb@privateproject
Using the awesome tool awsume (https://github.com/trek10inc/awsume) you may change the current credentials with
awsume accounta
And git push will work nevertheless, because the codecommit helper chooses the right profile.
The whole story:
mkdir privateproject
cd privateproject
awsume accountb
aws codecommit create-repository --repository-name "privateproject" --region eu-central-1
git init .
echo "hi" >readme.md
git add readme.md
git commit -m "If you can read this, congrats"
git branch main
git checkout main
git remote add origin codecommit::eu-central-1://accountb@privateproject
git push --set-upstream origin main
And you get all code safely stored in AWS:
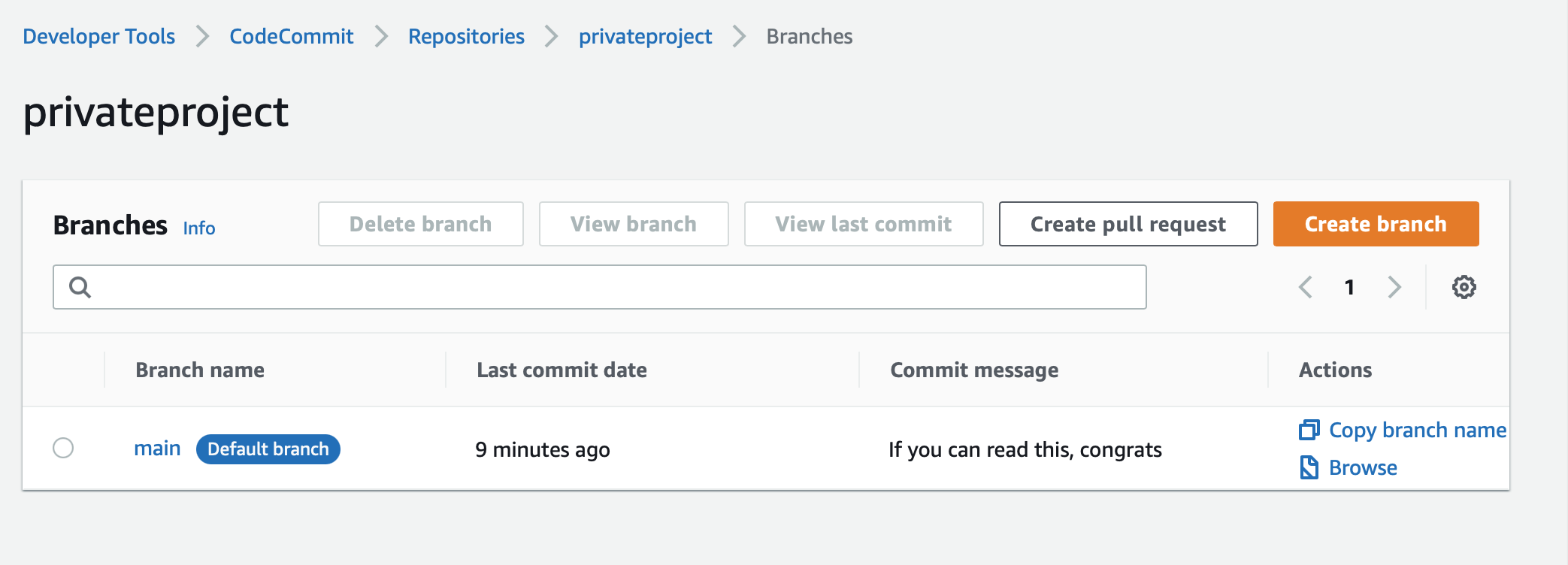
This also works fine with assumed role. But it will not work with SSO.
SSO
When you use AWS SSO on the console, you can copy&paste the credentials, but you have no profiles, so
git remote add origin codecommit::eu-central-1://accountb@privateproject
is not an option - so road closed.

Ben helps
aws-sso-util to the rescue. I have worked with sso and the tool (https://github.com/benkehoe/aws-sso-util) now several weeks. It really helps.
After configuring the sso on AWS side aws-sso-util can find all the different sso accounts and fill all needed configuration with:
aws-sso-util configure populate --region eu-central-1
Example for an entry in ~/.aws/config
[profile accountb]
sso_start_url = https://mcu.awsapps.com/start/
sso_region = eu-central-1
sso_account_name = test
sso_account_id = 911555475555
sso_role_name = AdministratorAccess
region = eu-central-1
credential_process = aws-sso-util credential-process --profile accountb
sso_auto_populated = true
Daily Work
With all things configured, you may use the tool from the command line:
- Login
aws-sso-util login
This opens the browser, you login once in the sso and your console session is configured.
- Switch Account
Now you can switch to the configured accounts in the sso
awsume accountb
- Pull/Push to codecommit in other account in the same sso
And with configured aws-sso account in the git settings, you always push to the right repository:
cat .git/config
...
[remote "origin"]
url = codecommit::eu-central-1://accountb@privateproject
fetch = +refs/heads/*:refs/remotes/origin/*
[branch "main"]
remote = origin
merge = refs/heads/main

Final words
AWS SSO is a safe and powerfull way to handle multiple accounts within an organisation. I have shown you how you may use CLI tools with that approach also.
If you have any comments, please contact me on twitter, stay safe, thanks for reading.
Thanks
To Ben Kehoe for his tool.
Photo by NeONBRAND on Unsplash
Photo by Ben Wicks on Unsplash
Photo by call me hangry 🇫🇷 on Unsplash
